Working of NTLM Authentication
- kkalvani
- Oct 23, 2024
- 2 min read
While I was studying one of the modules in the CEH - Certified Ethical Hacker course, I came across a few interesting concepts within Windows systems, one of which is the NTLM authentication.
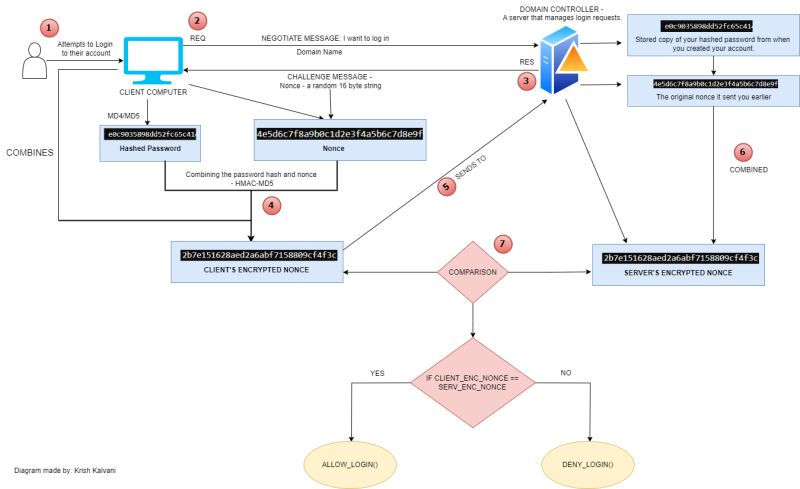
As most of us are Windows users, it is crucial for us to understand how NTLM works and how our passwords get authenticated when we log in to our Windows account. Please refer to the diagram I have made for better understanding.
We have two main components:
1) The client computer - used by the user.
2) The domain controller - This manages login requests. When you create your account for the first time and set up your password, this device stores a copy of your password for future authentication.
When the user enters their password and clicks "sign in", their computer at the backend, will hash their password using either the MD4 or MD5 algorithm. While this happens, a "Negotiate" message is sent (example: "I want to log in") to the domain controller.
Upon receiving this from the client, the domain controller sends a response which contains the "Challenge" message i.e., a random 16-byte string called a Nonce. When the client computer obtains this "Nonce", it will combine the "hashed password" that the user typed, with this nonce. This formulates a new encrypted string (the client's encrypted nonce).
The client sends this result to the domain controller.
Now, we know that the domain controller has a copy of the user's hashed password along with the original nonce it sent to the client earlier. The domain controller combines these two and creates its own new encrypted string (the server's encrypted nonce).
The client's encrypted nonce is compared with the server's encrypted nonce. If they are exactly the same, the user is authenticated to access the computer.
There are mainly two versions of NTLMs i.e., NTLMv1 and NTLMv2. The main differences between them are their strength of encryption.
This type of authentication is outdated and is replaced by Kerberos authentication, but it still widely supported in Windows systems for backward compatibility.
NTLM authentication contains weaker encryption and is prone to replay attacks, where you can use a tool like Wireshark to capture authentication messages and reuse them to gain unauthorized access, or pass-the-hash attacks where you can use Mimikatz to obtain the NTLM hash of a user's password and use it to authenticate without needing to know the actual password. To dive in further into the hash, attackers may use Responder or John the ripper to crack (translate) the hash. Which is why nowadays, we find most Windows systems using the stronger encrypted and more difficult to crack (more secure), Kerberos authentication.




Comments