Understanding Active Directory: From User Objects to Group Policy Management
- kkalvani
- May 8, 2025
- 6 min read
1.INTRODUCTION
In technical terms, the word 'directory' is basically a hierarchal structure that stores information about ‘objects’ on a network. An object is like a record in a database, made up of attributes (key-value pairs). These "objects" represent specific entities in an organization or company, such as users, computers, groups, and more. Each of these entities contain attributes related to them. We will see how it looks later in this article.
2.WHAT IS ACTIVE DIRECTORY?
A directory service like an Active Directory Domain Service (AD DS) is a Microsoft service/platform that does exactly what a directory does i.e., stores and organizes information about network resources such as users, computers, groups, and devices in a hierarchical structure. Active Directory runs on Windows Servers, therefore, becomes a Domain Controller. It acts like the central brain of a company's IT network, and it controls who can access what, where, and how (secure database + policy engine). The Active Directory, when installed on the Windows Server, will create an "ntds.dit" database file which will store all the hierarchy information and other sensitive information (hashed passwords) that cyber-attackers aim to obtain during an attack.
Admins can modify AD structures (like creating users, OUs, or policies) and manage the 'objects' whereas normal users do interact with AD every time they log in to get authenticated (Kerberos/NTLM), or to access files and permissions. This helps manage and authenticate users, computers, and resources within a networked environment.
3.ACTIVE DIRECTORY STRUCTURE EXAMPLE
To keep the environment organized, objects are placed into Organizational Units (OUs) - which act like folders, typically representing departments, branches, object containers, or functional teams.
Here is a labelled hierarchal structure of an example fictional firm – KalvTech Technologies and how its AD infrastructure is looking like in the back end.

Here, we can see that this firm has a Head Office branch (the first OU), in which has an IT and an HR department (two more OUs). In this example, we will stick to one branch and two departments in it to better understand how Active Directory works. But just know that there can be more branches and more departments per branch.
Diving into the IT OU (IT department), that is in the Head Office OU, we have three more OUs i.e., Users, Computers, and Groups. In each of these OUs, we have our objects i.e., the individual user, computer and group details.
There can be many users (User Objects) in the Users OU, many computers (Computer Objects) in the Computers OU, and many Groups (Group Objects) in the Groups OU.
Each user object for example – John, being the admin, would look like:

It would be the same for David and Mary but with their details specified and they would be in the IT-Users group.
For a computer, IT-PC01 for example, it would look like:
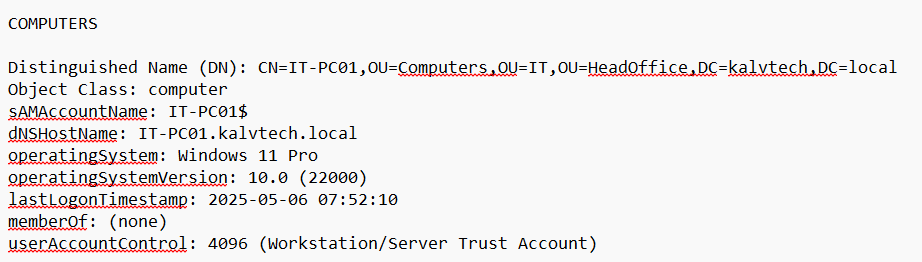
For the groups made in KalvTech, there are two groups for the IT department, so this is how their objects may look:
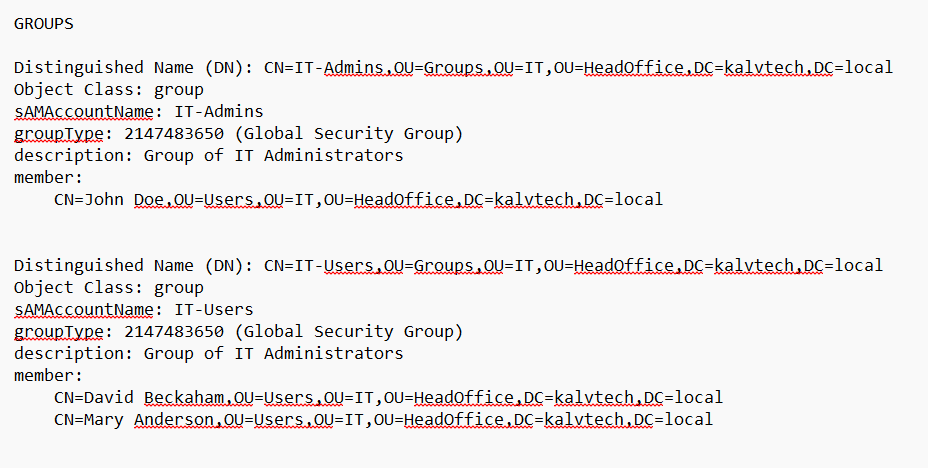
It’s the same concept for objects belonging in any other departments (HR, Finance, Sales, etc.) and other branches (London, Tokyo, etc.).
All these user, computer, and group objects in Active Directory are stored within the Active Directory database file named ntds.dit. This database file resides by default in the C:\Windows\NTDS folder on a domain controller. Alongside this database file, there are transaction logs and other supporting files in the same folder that help maintain data integrity and enable replication across other domain controllers (for synchronization). The entire directory information, including user, computer, and group objects, is contained within this single database file on the domain controller's file system.
4.POLICY ENFORCEMENT
Now, for Group objects, is where we use the Active Directory to create groups for who should be added as the admin (IT-Admin) and who should be added as a regular IT employee (IT-User). We implement their privileges using Group Policy Objects (GPOs).
GPOs are set-up via the organization’s Group Policy Management Console (GPMC).
The Group Policy Management Console (GPMC) is the centralized tool used to create, manage, and link Group Policy Objects (GPOs) across Active Directory, but the actual policy settings (like enabling RDP, blocking USBs, etc.) are configured inside the GPOs themselves using the Group Policy Management Editor.
In GPMC, you create or select a GPO.
You then edit that GPO with the Group Policy Management Editor to define specific settings (such as enabling Remote Desktop or restricting USB usage).
After configuring the settings inside the GPO, you link the GPO to an Active Directory container (site (branch), domain, or OU) via GPMC to apply those settings to the users or computers within that container.
GPMC also lets you apply security filtering and enforce policies and ACLs towards specific groups (admin or regular users).
So, we simply link the following GPOs to the IT OU:
Allow RDP and PowerShell (Security filtered to: IT-Admins)
Restrict Control Panel and USB (Security filtered to: IT-Users)
The most important thing here is to perform "Security Filtering" on the GPOs to ensure that RDP and PowerShell are only allowed for IT-Admins and not IT-Users. Similarly, security filtering should be done for IT-Users to restrict control panel and direct USB attachment (for example).
Otherwise, the entire IT department would have all the admin privileges, which would violate the Principle of Least Privilege rule.
In the case of the HR department i.e., HR OU (in the AD’s perspective). This just has one user object that uses one computer object and a GPO to enforce a strict password policy and no direct USB attachments.
5.GENERALIZED AD STRUCTURE
Now that we have covered how each component in an AD works, we can view the big picture of how an organization’s set up would work with Active Directory:
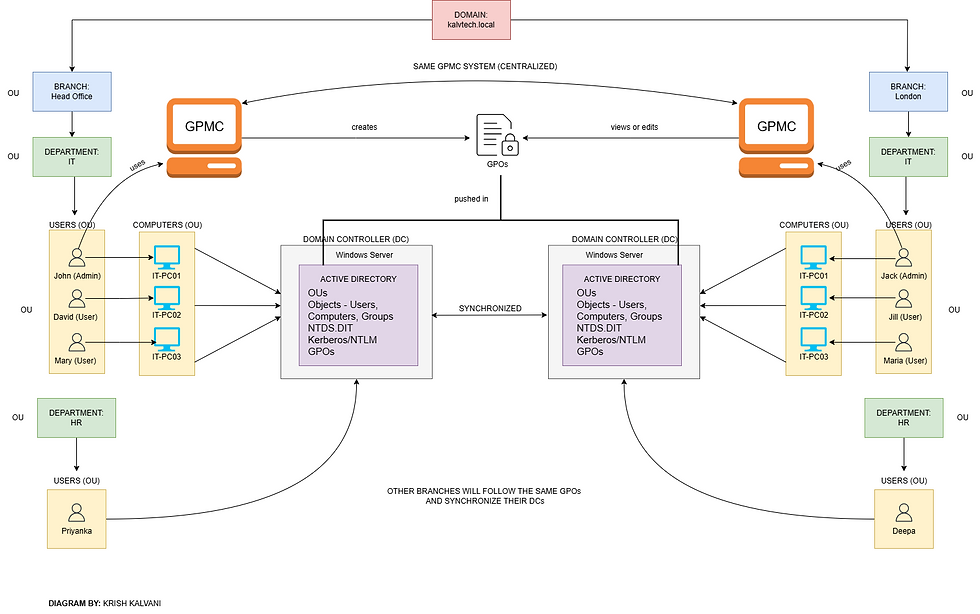
In the above diagram, the IT admins of both branches use a centralized GPMC and manages the GPOs of their respective assets. The domain controllers of each branch are synced together, using the same GPOs for their assets. Once created, these GPOs replicate automatically to all other domain controllers, including those in remote sites like London. Admins at other sites (e.g., London) can then use GPMC to view, modify, or create additional GPOs scoped and linked to their OUs or sites (so it won’t affect other branches), but the initial baseline GPOs usually originate from the Head Office or central IT team.
These GPOs are pushed into their Active Directories and when a user logs into their system, the corresponding GPO will be pushed from the DC to the user’s computer (account when logged in), thus, enabling the right permissions to the right user (detailed in Section 6).
AUTHENTICATION AND AUTHORIZATION PROCESS (HOW IT ALL WORKS TOGETHER)
When a user logs into their computer in an Active Directory (AD) environment, the process involves both authentication and authorization working together to enforce policies and privileges:

Authentication:
The user enters their credentials (usually username and password) on their computer (the computer object).
The computer sends an authentication request to a Domain Controller (DC) with those credentials typed.
AD uses protocols like Kerberos or NTLM to verify the user's identity without sending the password in clear text.
For Kerberos, the DC's Key Distribution Center (KDC) issues a Ticket Granting Ticket (TGT) to the user after validating credentials. This ticket is used to request service tickets for accessing resources securely.
The user's password is hashed (using MD4 for NT hash) and stored securely in the NTDS.dit database on the domain controller.
For authentication, the domain controller verifies the user’s credentials by comparing the processed password against the stored hash without ever transmitting or exposing the plaintext password.
Authorization:
Once authenticated, the user's identity and group memberships (like IT-Admin or IT-User) are used to determine authorization.
Based on the user's group membership, OU, and security filtering, the corresponding Group Policy Objects (GPOs) linked to those OUs are applied to the user's computer and account, enforcing the relevant policies and privileges.
This ensures that only authenticated users with proper authorization can access or perform actions on resources.
CONCLUSION
We are living in a world where lots of big-time companies use Microsoft’s Active Directory services, therefore, it is crucial for any cybersecurity professional to understand the basics of AD, understand how it's components work together, how the policies are applied to the right people, and lastly how the authentication and authorization works.
Having this foundational knowledge enables us to understand the importance of Active Directory and why it must be protected against cyber-attackers at all times.
REFERENCES
alvinashcraft (no date) User Object Attributes - Win32 apps. Available at: https://learn.microsoft.com/en-us/windows/win32/ad/user-object-attributes (Accessed: 2 May 2025).
Archiveddocs (no date) Directory data store: Active Directory. Available at: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc736627(v=ws.10) (Accessed: 2 May 2025).
How Authentication Works in Active Directory (2024) IS Decisions. Available at: https://www.isdecisions.com/en/blog/mfa/how-authentication-works-in-active-directory (Accessed: 2 May 2025).
meaghanlewis (no date) Active Directory Domain Services overview. Available at: https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/get-started/virtual-dc/active-directory-domain-services-overview (Accessed: 2 May 2025).
Narayanan, B. (2021a) ‘Active Directory Group Object Management’, Windows Active Directory, 2 March. Available at: https://www.windows-active-directory.com/active-directory-group-objects-management.html (Accessed: 3 May 2025).
Narayanan, B. (2021b) ‘User authentication and user authorization process: An explanation’, Windows Active Directory, 1 March. Available at: https://www.windows-active-directory.com/user-authentication-and-user-authorization-in-ad-html.html (Accessed: 3 May 2025).
What is a Group Policy Management Console and how does it work? – TechTarget Definition (no date) SearchWindows Server. Available at: https://www.techtarget.com/searchwindowsserver/definition/Group-Policy-Management-Console (Accessed: 3 May 2025).




Comments